While the deep web may have a reputation for illicit activities, there is actually a lot of legal content worth seeing. There are subtle distinctions between the deep web and the dark web, but this article really applies to both. However, be warned that the dark web is where you’ll find the internet’s worst criminal activity. If you intend on using our anonymity tips for taking part in illegal dark web activities, be warned that you can and probably will be caught.
The deep web is typically accessed with the Tor network, which means using the Tor browser. Technically speaking, the Tor browser is a modified version of Firefox. Tor is around 95% code from Firefox, but it has been modified at the source level in several ways. Additionally, Tor browser comes pre-installed with HTTPS Everywhere, a specially configured NoScript plug-in, and Tor connects to the Tor network (similar but different in many ways to a VPN). For additional explanations of online security and threats, you can read this website, Better Defend, that covers many useful topics.
However, even with all these out-of-the-box configurations for anonymity, there are extra steps to take to enhance your anonymity on the Tor network. You can never really be 100% anonymous on the internet, even with Tor – but there are things that will add layers of security around you. That’s what we’ll be focusing on in this article. So without further explanation, let’s get into how to protect your identity on the deep web.
Tor over VPN versus VPN over Tor
- Tor over VPN: You > VPN > Tor > Internet
- VPN over Tor: You > Tor > VPN > Internet
While the Tor network is similar to a VPN, it is ultimately not an actual VPN. A VPN and Tor can actually be combined, though the manner in which you combine them can offer different benefits and drawbacks.
Many people suggest connecting to a VPN before connecting to the Tor network. Connecting to a VPN before Tor gives you the benefit of hiding your browsing habits from your ISP (a major plus for pirates). It also means that Tor entry nodes cannot track you via IP address.
The drawback is that by connecting to a VPN before Tor, you are giving the VPN provider your actual IP address. You will also be vulnerable to malicious Tor exit nodes, particularly if you are not connected to HTTPS websites. To use VPN before Tor, you should strongly trust your VPN provider.
If you do the opposite configuration and connect to Tor before VPN, this masks your IP address from the VPN provider. Your traffic from Tor exit nodes becomes encrypted as well. It’s a bit easier to spoof your geolocation, and you can access websites that typically block Tor exit node IPs.
The drawback of Tor before VPN is that it can significantly slow your browsing speed, and it is overall susceptible to end-to-end timing attacks (which can reveal your identity in a successful attack). Tor before VPN is typically used by people who do not trust their VPN provider, but still want to use one.
Disable JavaScript
There are several known JavaScript vulnerabilities that can be exploited to de-anonymize Tor users. Thus, it is highly recommended to disable JavaScript within the Tor browser.
To disable JavaScript in Tor, type About:Config in the URL bar.
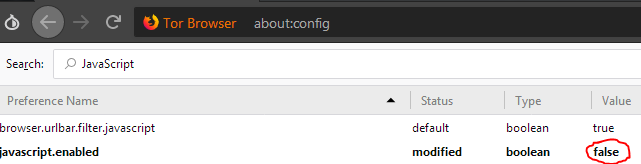
Then in the search bar, type ‘JavaScript’. You should see a line ‘javascript.enabled’ with the value ‘True’. Double click it to change the value to ‘False’.
The drawback of disabling JavaScript is that it may break some websites that depend on JavaScript to deliver parts of their content. Such websites may not properly load, in which case, you can add them to a whitelist to allow their scripts to load. However, by doing so, you allow your whitelisted website to act as cookies that can identify you. You should only allow JavaScript on websites if you have an extremely compelling reason to do so.
Additional Tips
Don’t use P2P over Tor: The Tor network is not built for P2P file sharing. By using P2P within Tor, you allow your Torrent client to send your IP address to the Torrent trackers and peers.
Don’t access your real accounts: While you are using the Tor browser, you should never access any of your real accounts. This means email, social media, Paypal, anything at all that you use outside of the Tor browser. It’s like wearing a Halloween mask to cover your face, and then putting a nametag on your shirt.
Regularly delete cookies: You should make a habit of regularly destroying cookies that you may obtain from websites. Some websites may recommend a plug-in like Self Destructing Cookies, but the Tor developers do not recommend using 3rd-party add-ons in the Tor browser. The Tor browser automatically deletes all cookies when you close the browser. You can also click the “New Identity” button within Tor to erase cookies as well.
Stay away from illicit websites: While the temptation of curiosity may be great, and you might want to see what all the fuss about drug trading and other illegal activities on the dark web is about, it is highly recommended to just stay away. Many of those “illegal” websites can actually be government agency “honeypots”, and the very act of connecting to those websites can get a knock on your door.
